Access Control List (ACL)

As you know there are some protocols that make your network powerful. These protocols give you abilities to manage your network and the traffic of data. Access Control List is a list of rules that specifies which users or systems are granted or denied access to a particular object or system resource.
This protocol is also installed in routers or switches. Where they act as filters, managing which traffic the network. in the rest of this article, we talk about ACL and what does it do!
Access Control List (ACL):
Each system resource has a security attribute that identifies its access control list. This list includes an entry for every user who can access the system. The most common privileges for a file system ACL include the ability to read a file or all the files in directory, to write to the file or files and to execute the file if it is an executable Linux and Windows. On a computer network, access control lists are used to prohibit or allow certain types of traffic to the network. they commonly filter traffic based on its source and destination.
What does ACL use for:
Access control lists are used for controlling permissions to a computer system or computer network. They are used to filter traffic in and out of a specific device. Those devices can be network devices that act as network gateways or endpoint devices that users access directly.
On a computer system, certain users have different levels of privilege, depending on their role. For example, a user logged in as network administrator may have read, write and edit permissions for a sensitive file or other resource. By contrast, a user logged in as a guest may only have read permissions.
Access control lists can help organize traffic to improve network efficiency and to give network administrators granular control over users on their computer systems and networks. Access Control Lists can also be used to improve network security by keeping out malicious traffic.
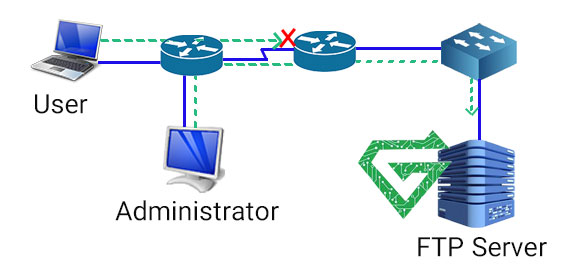
What are ACL Practices:
When configuring ACLs, you should adhere to a few best practices to ensure that security is tight and suspicious traffic is blocked:
- ACLs everywhere:
ACLs are enforced on each interface, in nearly all security or routing gear. This is fitting as you can’t have the same rules for outward-facing interfaces and interfaces that form your campus network. However, interfaces are similar and you don’t want some protected by ACLs and some exposed. The practice of an ACL on all interfaces is essential for inbound ACLs, specifically the rules that decide which address can transfer data into your network. Those are the rules that make a considerable difference. - ACL in order:
In almost all cases, the engine enforcing the ACL begins at the top and moves down the list. This has implications for working out what an ACL will do with a specific data stream. One reason organizations adopt ACLs is that they have a lower computational overhead than stateful firewalls and that they work at high speeds. This is essential when you try to implement security for fast network interfaces. However, the longer a packet remains in the system, while it is examined against the rules in the ACL, the slower the performance. The trick is to put the rules that you expect will be triggered at the top of the ACL. Work from the general to specific, while ensuring the rules are logically grouped. You should know that each packet will be acted on by the initial rule that it triggers, you could end up passing a packet via one rule when you intend to block it via another. Consider how you want the chain of events to happen, in particular when adding new rules. - Document your work:
When you add ACL rules, document why you are adding them, what they are intended to do, and when you added them. You don’t need to have one comment per rule. You can make one comment for a block of rules, an intricate explanation for a single rule, or a combination of both approaches. Developers should ensure that the current rules are documented, so nobody needs to guess why a rule is there.
How does ACL work:
Each ACL has one or more access control entries (ACEs) consisting of the name of a user or group of users. The user can also be a role name, such as programmer or tester. For each of these users, groups or roles, the access privileges are stand in a string of bits called an access mask. Generally, the system administrator or the object owner4 creates the access control list for an object.
A filesystem ACL is a table that informs a computer operating system of the access privileges a user has to a system object, including a single file or a file directory. Each object has a security property that connects it to its access control list. The list has an entry for every user with access rights to the system.
Typical privileges include the right to read a single file (or all the files) in a directory, to execute the file, or to write to the file or files. Operating systems that use an ACL include, for example, Microsoft Windows NT/2000, Novell’s Netware, Digital’s OpenVMS, and UNIX-based systems.
When a user requests an object in an ACL-based security model, the operating system studies the ACL for a relevant entry and sees whether the requested operation is permissible.
Networking ACLs are installed in routers or switches, where they act as traffic filters. Each networking Access Control List contains predefined rules that control which packets or routing updates are allowed or denied access to a network.
Routers and switches with ACLs work like packet filters that transfer or deny packets based on filtering criteria. As a Layer 3 device, a packet-filtering router uses rules to see if traffic should be permitted or denied access. It decides this based on source and destination IP addresses, destination port and source port, and the official procedure of the packet.
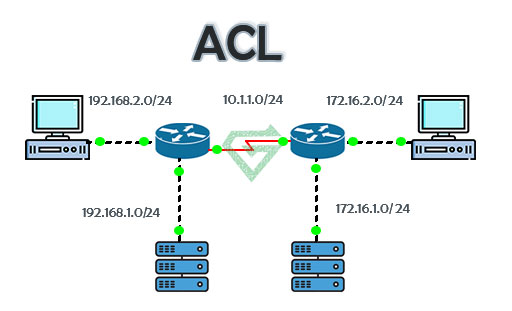
Types of Access Control:
Mandatory access control: Mandatory strict model is designed specifically for government offices and agencies. This strict and secure model is based on a hierarchy model. Users are assigned security and a clearance level to access resources, while objects are assigned a security label. Users can only access the resources they are permitted to according to their security level or the resources that fall under their hierarchy level.
Discretionary access control: Discretionary access control can be used in social networking, as there’s a frequent need to change the visibility of the content. This model offers flexibility and allows you to decide who can access your data. It also allows you to customize access policies according to each user.
Role-based access control: Role-based access control allows you to assign specific roles to employees according to their function within an organization. Moreover, these roles are aligned with access permissions rights. This type of control can be used when you need to share data with a particular department.
Attribute-based access control: Attribute-based control allows you to define a set of attributes, including resources, users, and objects. Using this model, access is granted to the user based on its role and attributes.
Rule-based access control: This type of control grants or denies access based on a predefined set of rules.
What are different types of Access Control List:
There are some types of categories of ACL in networking that we introduce them in rest.
- Standard ACL: Standard ACL is used to filter traffic based on the source IP address only. It is the most basic type of ACL and can be used to permit or deny traffic from a particular network or IP address. Standard ACLs are typically used at the edge of a network to block unwanted traffic entering the network.
- Extended ACL: An Extended ACL is more flexible than a standard source and destination IP addresses, protocols, ports and other parameters. Extended ACLs are more commonly used than standard ACLs and are typically implemented on internal network devices, such as routers to control traffic between different network segments.
- Dynamic ACL: Dynamic ACLs are often known as Lock and Key, and they can be used for specific attributes and timeframes. They rely on extended ACLs, authentication, and Telnet for their functionality.
- Reflexive ACL: Reflexive ACLs are also known as IP session ACLs. They filter IP traffic based on upper-layer session information. These ACLs can only be used to permit IP traffic generated within your network and deny the IP traffic generated from an external or unknown network.
- Time-based ACL: Time-based ACLs are similar to extended ACLs. However, they can be implemented by creating specific times of the day and week.
For explain more to Standard and Extended ACLs, there is also a Named ACL, which is simply an ACL that is given a specific name for easier identification and management. Named ACLs can be either standard or extended depending on the criteria used for filtering traffic.
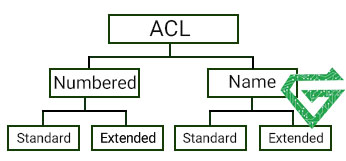
A standard ACL list is generally implemented close to the destination that it is trying to protect. Extended access control lists are generally implemented close to the source. Extended ACLs can be configured using access list names instead of access list numbers.
Router (config)# access-list (1300-1999) (permit | deny) source-addr (source-wildcard)
Benefits of Access Control List:
Simplified: user identification: an ACL simplifies the way that users are identified. Access Control Lists ensure that only approved users and traffic have access to a system.
- Performance: ACL provides performance advantages over other technologies that perform the same function. They are configured directly on the routing device’s forwarding hardware, so access control list does not have a negative performing effect on routing devices. Also, controlling network traffic enables networks to be more efficient.
- Control: ACL can give administrators more granular control over user and traffic permissions on a network at many different points in the network. they help control access to network endpoint and traffic following between internal networks.
Where can you place an access control list?
Access control lists can be placed on virtually any security or routing device, and having multiple ACLs in different parts of the network can be beneficial.
ACLs are well suited to network endpoints — like applications or servers — that require high speed and performance, as well as security.
Network administrators may choose to place an access control list at different points in the network depending on the network architecture. ACLs are often placed on the edge routers of a network because they border the public internet. This gives the Access Control List a chance to filter traffic before it reaches the rest of the network.
Edge routers with ACLs can be placed in the demilitarized zone (DMZ) between the public internet and the rest of the network. A DMZ is a buffer zone with an outward-facing router that provides general security from all external networks. It also features an internal router that separates the DMZ from the protected network.
Why do we use ACL?
- Controlling traffic flow
- Restricted network traffic for better network performance
- A level of security for network access specifying which areas of the server/ network and service can be accessed by a user and which cannot
- Granular monitoring of the traffic exiting and entering the system
Conclusion:
ACL or Access Control List contains rules that grant or deny access to certain digital environments. Normally, ACLs were the only way to achieve firewall protection. Today, there are many types of firewalls and alternatives to ACLs.
However, organizations continue to use ACLs in conjunction with technologies like virtual private networks (VPNs) that specify which traffic should be encrypted and transferred through a VPN tunnel.
You can read other our blogs about network equipment and its protocols in Atech blog. Atech is a company that provides network equipment of valuable brands and high quality. if you need to equip your network, our team is here to help and consult you free.





