What is BGP and Why Is It Critical for the Internet

BGP is a primary routing protocol that makes the global internet possible. It connects thousands of independent networks and ensuring data knows how to travel from point A to B. BGP protocol is really important for the internet and network.
Some of network equipment use this protocol to have secure network, such as routers, firewalls, virtual appliances, cloud gateways and software routers. we are going to explain you about it. In the end, you can share your questions and opinions with us.
What is BGP and Why Is It Critical for the Internet:
For answering to this question, you must divide it to two parts. “What is BGP” and “Why is it Critical for the internet”. So, first of all, we will explain the definition of BGP and then work on its matter.
What is BGP?
BGP (Border Gateway Protocol) is the main routing protocol that manages how data is exchanged between different networks on the internet. It works between large networks called Autonomous Systems (AS), such as internet service providers (ISPs), cloud providers, and major organizations.
BGP determines the best path for data to travel across these systems, using rules and policies rather than just the shortest path. It runs over TCP and maintains a table of routes, allowing networks to make intelligent routing decisions.
Without BGP, there would be no structured way for internet traffic to move between independent networks, making global communication impossible.
- External Gateway Protocol: BGP is a path‑vector protocol that exchanges reachability info between ASes. It builds routes by recording the exact sequence of AS numbers (the “AS-path”) that data travels through.
- Runs over TCP port 179: Ensures reliable delivery and supports encrypted extensions (TLS, VPN).
The roles of BGP:
- Global Routing Backbone
Enables data exchange between different ISPs, content providers, enterprises, and governments. - Policy-Based Routing
Operators can control how their traffic flows using attributes like AS-path, MED, next-hop, local preference, enabling cost, performance, or compliance optimization. - Resilience & Redundancy
Supports multihoming networks connect to multiple ISPs and switch to alternate routes automatically during outages - Inter-AS Routing
BGP connects different Autonomous Systems (ASes), making it the core routing protocol of the internet.
- Path Vector Protocol
Instead of just choosing the shortest path, BGP uses AS-path information to make routing decisions and avoid loops.
- Loop Prevention
BGP prevents routing loops by rejecting routes that contain the local AS in the AS-path.
- Scalability
BGP can handle hundreds of thousands of routes, which makes it ideal for large networks like ISPs and cloud providers.
- Route Aggregation
BGP can combine multiple IP routes into a single advertisement using CIDR (Classless Inter-Domain Routing), reducing routing table size.
- Support for Multiple Paths
BGP can maintain multiple routes to a destination, though by default it uses only one (can be modified with multipath extensions).
- Reliable Communication via TCP
BGP uses TCP port 179 for reliable delivery of routing updates.
- Next-Hop Attribute
Indicates the IP address to reach a destination, important for both eBGP and iBGP routing.
- Support for Route Reflectors & Confederations
These features help simplify iBGP configurations in large-scale networks.
Why BGP Matters (and Why Problems Happen):
BGP matters because it is the backbone routing protocol that keeps the global internet connected. It allows thousands of independent networks such as internet service providers, cloud providers, and enterprises to exchange routing information and determine the best paths for delivering data across the world.
Without BGP, these networks wouldn’t know how to reach each other, and the internet would essentially fall apart into isolated sections. BGP also enables resilience by rerouting traffic during outages, supports policy-based routing to control traffic flow, and handles the massive scale of the modern internet. Simply put, BGP is essential for the speed, stability, and reach of everything we do online.
Foundational yet Trust-Based: BGP was built on trust. It lacks inherent validation, so misconfigurations or malicious route announcements called route leaks or prefix hijacks can cause massive outages or data interception.
Real Disasters: Notable examples include:
- YouTube hijacked by Pakistan Telecom (2008)
- Google Cloud and Cloudflare interruptions
- Facebook DNS outage in October 2021 after BGP withdrawals
Read more: Internet Control Message protocol (ICMP)
Securing of BGP:
BGP is vulnerable to attacks that exploit false routing information. For instance, attackers can overwhelm a router with illegitimate traffic in a denial-of-service (DoS) attack, disrupting its ability to function.
Even more dangerously, an attacker can falsely advertise ownership of IP address blocks a tactic called BGP hijacking which allows them to redirect, intercept, or block traffic intended for another network.
Since BGP was not originally designed with strong security, it’s possible for malicious actors to temporarily take control of internet traffic using these methods.
- RPKI (Resource Public Key Infrastructure): Cryptographically validates that an AS is authorized to announce specific IP prefixes.
- Route Filtering & Best Practices: Initiatives like MANRS encourage ISPs to apply prefix filters, AS path validation, and maintain proper routing hygiene.
- Global Push: Governments (like the U.S.) and bodies like FCC are urging tighter BGP security to defend against state-level manipulation.
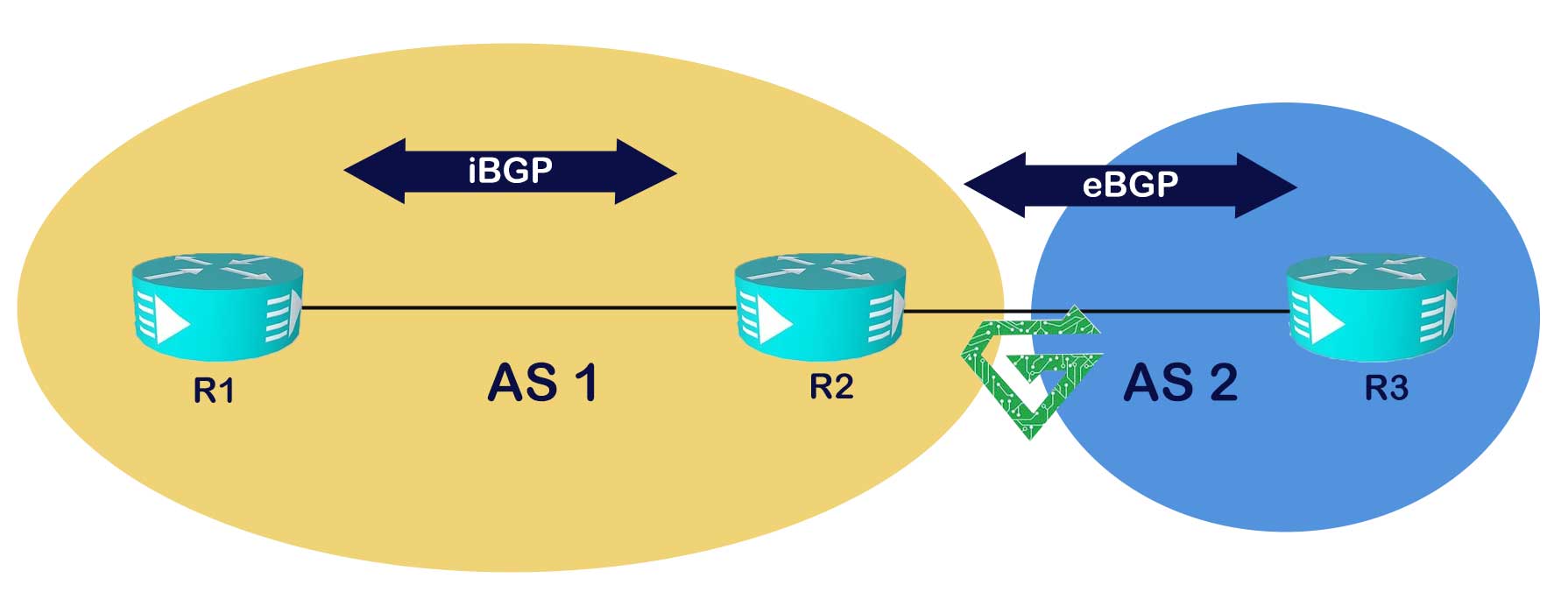
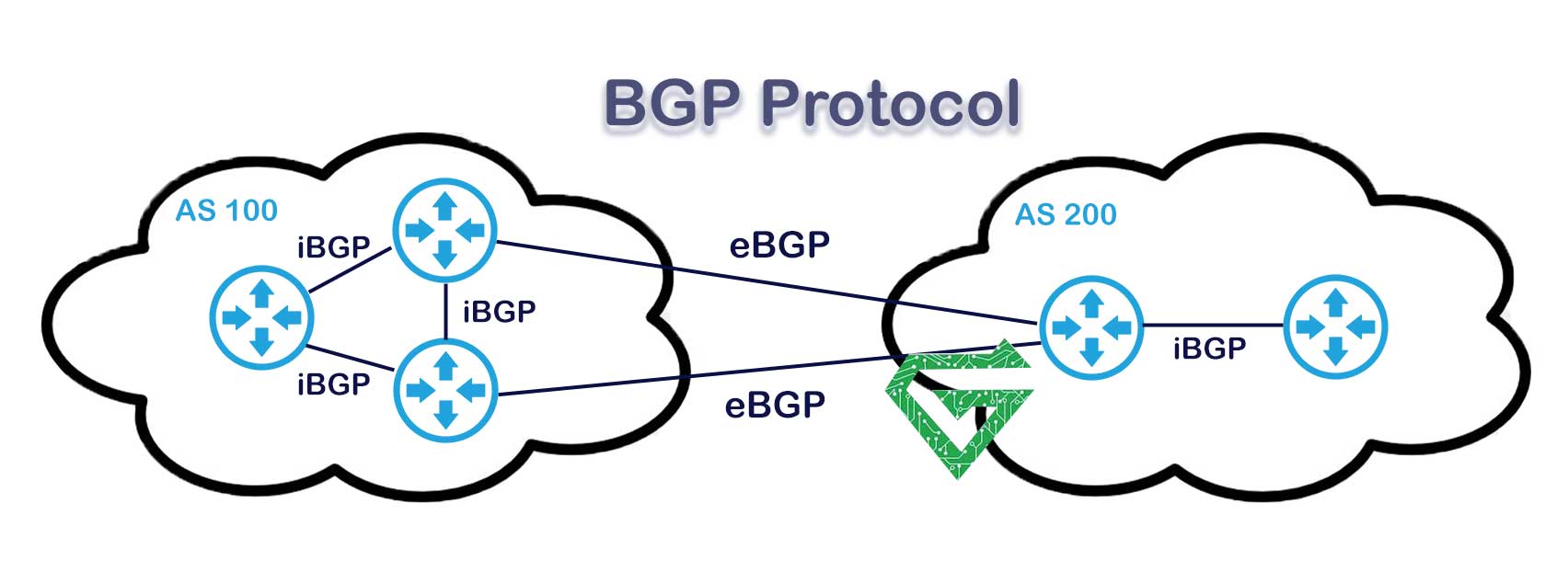
Difference Between External BGP (eBGP) and Internal BGP (iBGP):
External BGP (eBGP) and Internal BGP (iBGP) are two types of Border Gateway Protocol used in different contexts within internet routing. eBGP is used to exchange routing information between different Autonomous Systems (AS), such as between two internet service providers or between an ISP and a customer network.
In contrast, iBGP is used within a single AS to share routing information among routers that belong to the same organization. While eBGP is typically used for connecting external networks, iBGP helps maintain consistent routing internally.
A key difference is that eBGP peers often modify the next-hop information and automatically share routes, while iBGP peers require full-mesh connections or route reflectors and do not automatically advertise routes to each other. Both are essential for making sure data finds the best and correct path through the internet.
What is an Autonomous System (AS)?
An Autonomous System (AS) is a large network or group of networks that is managed by a single organization and follows a unified routing policy. Each AS is assigned a unique AS number (ASN), which identifies it on the internet. Autonomous Systems use BGP to exchange routing information with other ASes.
Simple Example:
Think of an AS like a city with its own road rules. It connects to other cities (other ASes) via highways (BGP), but inside the city, it controls how traffic flows (using internal routing protocols like OSPF or EIGRP).
Real-world examples of ASes:
- Google: AS15169
- Cloudflare: AS13335
- Iran Telecommunication Company: has its own ASN
- Your university or large company: may also have an AS if it connects directly to the internet
How BGP Works:
BGP (Border Gateway Protocol) works by enabling routers in different networks (called Autonomous Systems) to exchange routing information and determine the best paths for sending data across the internet. When two BGP routers connect (called BGP peers or neighbors), they form a BGP session using TCP port 179. Once the session is established, they exchange information about which IP prefixes (networks) they can reach and through which paths.
Each route is advertised with attributes like:
- AS Path (list of ASes the route has passed through)
- Next-Hop (IP address to reach the destination)
- Local Preference
- MED (Multi-Exit Discriminator), etc.
BGP doesn’t simply choose the shortest route; instead, it selects the “best” route based on these attributes and custom policies set by network administrators. If a link fails or a better route becomes available, BGP updates its routing table and propagates the change to its peers.
To prevent loops, BGP checks the AS Path if a router sees its own AS in the path, it rejects the route. Within an organization (using iBGP), routes are shared internally, and between organizations (using eBGP), BGP manages external traffic exchange.
Read more: OSPF (Open Shortest Path First) Protocol
How does the Border Gateway Protocol handle scale?
The Border Gateway Protocol (BGP) is designed to handle the massive scale of the global internet by using several key mechanisms. First, it supports route aggregation, which allows multiple IP addresses to be summarized into a single advertisement, helping reduce the size of routing tables.
BGP also sends only incremental updates, meaning it shares changes in routing information rather than re-sending the entire table each time this keeps communication between routers efficient. Internally, in large networks, BGP uses features like route reflectors and confederations to avoid the complexity of a full mesh of connections between routers.
Additionally, BGP uses attributes such as AS Path, Local Preference, and MED to make intelligent routing decisions, rather than simply choosing the shortest path. These features together make BGP capable of scaling to support thousands of networks and hundreds of thousands of routes, ensuring reliable and optimized routing across the global internet.
Common problems of BGP:
- Lack of Built-in Security
- BGP was built on trust, so routers accept routes without checking if they are legitimate.
- This allows route hijacking and route leaks, where incorrect routing info is spread either by accident or maliciously.
- Route Hijacking
- A network falsely advertises ownership of IP addresses it doesn’t control.
- Can lead to traffic interception, blackholing, or massive outages.
- Route Leaks
- When a network leaks internal routes to the public internet by mistake.
- This can misdirect traffic or overload smaller networks unintentionally.
- Slow Convergence
- When there’s a change (e.g., a route goes down), BGP can take minutes to update and settle on a new path.
- This delay is called slow convergence and can lead to temporary outages or unstable connections.
- No Loop Detection in iBGP
- iBGP relies on full mesh or route reflectors, and it doesn’t detect loops using AS Path (like eBGP does).
- Misconfigurations can create routing black holes or loops if not handled properly.
- Scalability and Complexity
- Large networks need complex BGP setups using route reflectors, confederations, and prefix filtering.
- Managing BGP at scale requires expertise, and mistakes can have global effects.
- No Built-in Authentication
- BGP doesn’t verify the identity of the peer beyond TCP.
- Although MD5 and TTL security exist, they are optional and rarely used.
Solutions of BGP:
- RPKI (Resource Public Key Infrastructure): to verify that a network is authorized to advertise a rote.
- MANRS (Mutually Agreed Norms for Routing Security): best practices for ISPs and operators.
- BGP monitoring tools: like BGPMon, RIPE RIS, or Cloudflare Radar.
Conclusion:
In conclusion, BGP (Border Gateway Protocol) is the backbone of global internet routing, enabling thousands of independent networks to communicate and exchange data efficiently. It not only determines the best paths for traffic across complex networks but also provides the flexibility and control needed to manage internet-scale routing.
Despite its challenges like security vulnerabilities and complexity BGP remains essential for the stability, scalability, and performance of the internet. Without it, the global connectivity we rely on every day simply wouldn’t be possible. If this article is useful for you, you can read our other articles in Atech Blog.





