Internet Control Message protocol (ICMP)

There are many protocols that help devices and network to communicate and troubleshooting the packet flow. The Internet Control Message Protocol (ICMP) is a fundamental component of the Internet Protocol Suite, primarily used for sending error messages and operational information regarding the success or failure of communication between IP devices.
Despite not being a transport protocol that carries application data, ICMP plays a critical role in network troubleshooting, diagnostics and management. This article will discuss the Internet Control Message protocol (ICMP) and its various uses.
Internet Control Message protocol (ICMP):
ICMP stands for Internet Control Message Protocol. It is defined in RFC 792 and works closely with the Internet Protocol (IP). While IP is responsible for routing packets from source to destination, ICMP is used to communicate issues that arise during this process. It is encapsulated within IP packets and is mainly used by network devices like routers and hosts to send notifications about network issues.
ICMP Protocol operates at the Network Layer (Layer 3) of the OSI model and is considered an integral part of the IP protocol. It is used to report problems such as unreachable destinations, routing loops and time exceeded errors. These messages help administrators identify and resolve network problems more effectively.

Features of ICMP:
- Error Reporting: ICMP is designed to report errors that occur during packet delivery. It informs the sender about problems that prevent successful delivery.
- Diagnostic Tools: Utilities like “ping” and “traceroute” rely on ICMP to measure latency and trace the route packets take to reach their destination.
- No Authentication: ICMP lacks built-in security features, making it susceptible to abuse in network attacks like ICMP floods.
- Not for Data Transmission: Unlike TCP or UDP, ICMP Protocol is not used to transmit application data but only to send control and error messages.
Common types of ICMP:
ICMP messages are identified by type and code values. Some of the most common types include:
- Echo Request and Echo Reply (Type 8 and 0)
- Used in the “ping” command to test connectivity between two devices.
- Destination Unreachable (Type 3)
- Sent when a destination is unreachable due to issues like network failure, host down, or protocol not supported.
- Time Exceeded (Type 11)
- Indicates that the TTL (Time to Live) of a packet has expired, often used in traceroute operations.
- Redirect (Type 5)
- Suggests a better route for the packet, typically sent by routers.
- Source Quench (Type 4) (Deprecated)
- Once used to indicate network congestion, but now deprecated due to inefficiency and abuse potential.
Type 12: Parameter Problem: Indicates an error in the IP header of a packet.
Type 13: Timestamp Request & Type 14: Timestamp Reply: Used to measure time delays between devices.
How does ICMP work?
ICMP works by sending control messages between network devices to report errors and provide information about network conditions. When a problem occurs during the delivery of IP packets such as a router being unreachable, a destination not responding, or a packet’s time-to-live (TTL) expiring ICMP generates a message and sends it back to the source device.
These messages are encapsulated inside IP packets but do not carry user data. For example, when you use the “ping” command, your device sends an ICMP Echo Request to the target, which responds with an ICMP Echo Reply if it’s reachable.
This helps verify connectivity and measure round-trip time. ICMP thus plays a behind the scenes role in network diagnostics and error reporting, helping maintain the reliability and efficiency of IP communication.
Read more: All about MPLS Protocol
ICMP in Network Troubleshooting:
Network administrators frequently use ICMP-based tools for troubleshooting. The two most common tools are:
- Ping: Sends ICMP Echo Requests and listens for Echo Replies. Helps determine if a host is reachable and measures round-trip time.
- Traceroute: Uses ICMP Time Exceeded messages to map the path that packets take to reach a target destination. Helps identify where delays or failures occur along the route.
These tools are essential in diagnosing problems like packet loss, latency, or network outages.
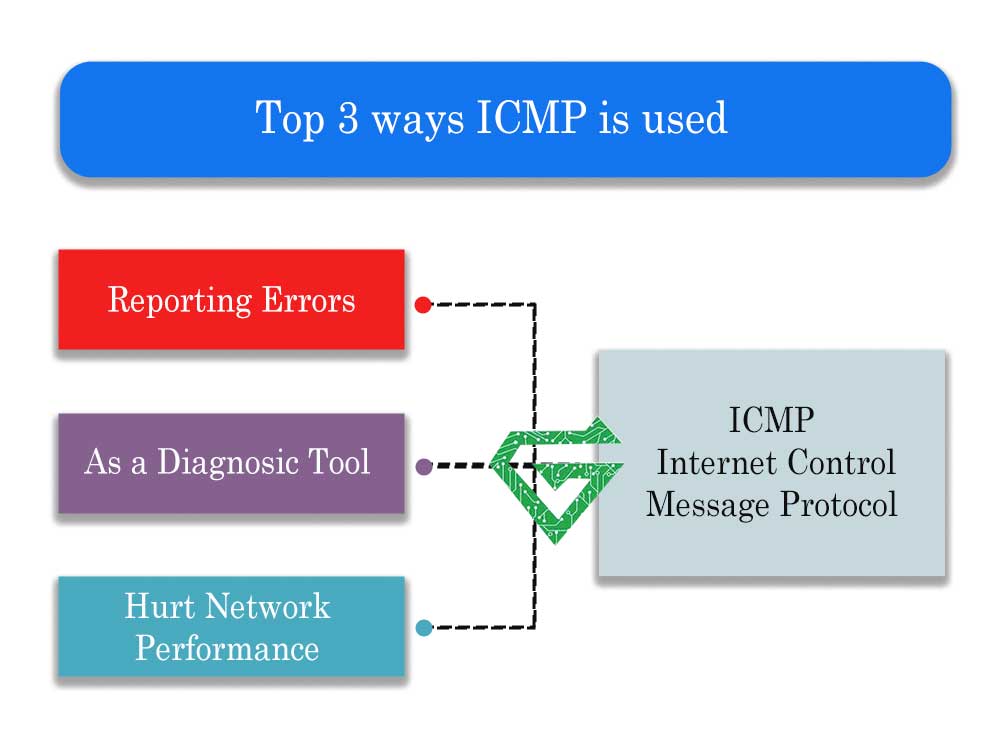
ICMP Protocol is used for:
Network Troubleshooting
- Ping: To check if a device (like a server or router) is reachable.
- Traceroute: To see the path packets take from your device to another.
Reporting Errors
- ICMP Protocol tells you if something goes wrong when sending data (e.g., “host unreachable,” “time exceeded”).
Network Diagnostics
- Helps identify problems like delays, dropped packets, or broken routes.
Packet Control
- It may inform the sender to slow down or take a better route (e.g., with “redirect” messages).
Security Concerns with ICMP:
While ICMP is useful for diagnostics, it also presents security risks if misused:
- ICMP Flood Attack: A form of Denial of Service (DoS) attack that overwhelms the target with ICMP Echo Requests.
- Ping of Death: Sends malformed or oversized packets that crash the target system.
- Smurf Attack: Spoofs ICMP requests to broadcast addresses, flooding the victim with Echo Replies.
To mitigate these threats, network administrators often filter or rate-limit ICMP traffic using firewalls or intrusion detection systems.
Read more: Man-in-the-Middle (MITM) Attack
How is ICMP used in DDoS attacks?
ICMP can be exploited in DDoS (Distributed Denial of Service) attacks to overwhelm a target system or network by flooding it with excessive ICMP traffic. Here’s how it’s typically used:
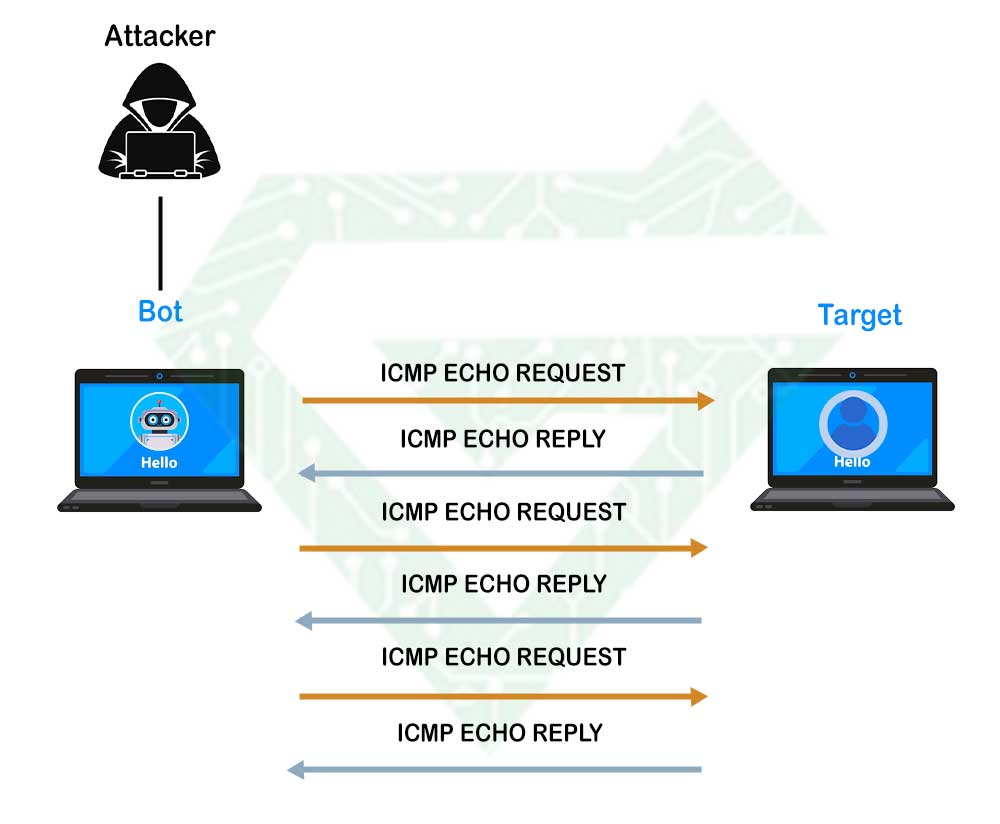
- ICMP Flood Attack (Ping Flood):
Attackers send a massive number of ICMP Echo Requests (like a flood of pings) to a target system from multiple compromised devices (a botnet). The target tries to reply to each request with an Echo Reply, consuming its CPU and bandwidth until it becomes unresponsive.
- Smurf Attack:
In this method, attackers send ICMP Echo Requests to a broadcast address (a message sent to all devices on a network), but they spoof the source IP to be the victim’s IP. Every device on the network then replies to the victim, overwhelming it with responses.
- Ping of Death (PoD):
This older attack involved sending malformed or oversized ICMP packets that could crash or freeze systems with poor packet-handling code. It’s mostly ineffective today due to modern system protections.
Why ICMP is Targeted:
- It’s easy to generate and transmit.
- It’s often left open for legitimate diagnostics (like ping).
- Many systems prioritize responding to ICMP, making them vulnerable.
Prevention:
- Rate-limiting or blocking ICMP at firewalls.
- Disabling responses to ICMP on public-facing systems.
- Using intrusion detection/prevention systems (IDS/IPS).
ICMP vs. Other Protocols:
ICMP is different from transport protocols like TCP and UDP:
- TCP: Provides reliable, connection-oriented communication with error checking and flow control.
- UDP: Offers fast, connectionless communication without guarantees of delivery.
- ICMP: Not used for delivering application data but for sending error messages and operational information.
Thus, ICMP complements other protocols by providing a mechanism for reporting issues in packet delivery.
Different versions of ICMP:
There are different versions of ICMP for different IP protocols:
- ICMPv4: Used with IPv4 networks. Defined in RFC 792.
- ICMPv6: Used with IPv6 networks. Includes additional features like Neighbor Discovery Protocol (NDP) and Multicast Listener Discovery (MLD).
These variants ensure that ICMP can function efficiently across both IPv4 and IPv6 environments.
Conclusion:
The Internet Control Message Protocol (ICMP) is a vital part of the Internet Protocol Suite, enabling error reporting, diagnostics, and network management. While it doesn’t handle user data like TCP or UDP, its role in maintaining the health and functionality of a network cannot be overstated. Understanding ICMP is crucial for network engineers and IT professionals who need to diagnose problems and optimize network performance.
By leveraging tools like ping and traceroute and understanding the different ICMP message types, professionals can effectively troubleshoot and secure their networks. As networks grow in complexity, the importance of robust diagnostic protocols like ICMP Protocol continues to rise.
ICMP gives network equipment such as router, network switch, server and .. a way to communicate problems, assist with troubleshooting, and guide packet flow, making it essential for maintaining healthy, efficient networks. Any devices with an IP Address can use this protocol to help detect and report communication issues. ICMP is an essential tool in every network.





